Introduction: Hidden Threats in Infrastructure
A series of recent security incidents in Europe have sounded an alarm throughout the global energy industry. When Norway, Denmark, and the UK successively launched security reviews of Chinese-manufactured critical infrastructure, a deeper issue emerged: our energy future is being threatened by an overlooked risk—the loss of data control authority.
This is not merely a technical issue. This is a fundamental problem that the entire global energy infrastructure must confront: when your energy storage system’s data is remotely stored, remotely managed, and remotely accessed, you have effectively surrendered your energy autonomy to an uncontrollable third party.
For UK and European energy operators, this question is no longer theoretical. It is regulatory, legal, strategic, and real.
Regulatory Storm Approaching
NIS2 Directive’s Mandatory Requirements
The EU’s Network and Information Systems Security Directive 2.0 (NIS2) officially took effect in October 2024. While this directive imposes mandatory cybersecurity requirements on all medium and large-sized energy companies, its core concern extends beyond mere “defense” to encompass data sovereignty and control authority.
NIS2’s requirements are unambiguous: critical infrastructure operators must possess complete understanding, audit capabilities, and control over data flows within their systems. When you cannot fully grasp where your data resides, who accesses it, and how it is used, you have violated the directive’s fundamental principles.
UK’s ESA Framework Coming Soon
The UK government plans to formally establish the Energy Security Act (ESA) framework in early 2026, which will set minimum cybersecurity and data protection standards for all energy storage systems within the UK. Preliminary signals suggest this framework will strongly favor local data control and local computing.
What does this mean? For operators currently using cloud-based systems, this signals a stark choice: either undergo system transformation within the next two years or face non-compliance risks.
GDPR and UK GDPR Data Protection Obligations
Many believe GDPR applies only to personal data. However, as energy storage systems grow increasingly intelligent, the data they generate—battery states, charge-discharge cycles, operational metrics—increasingly qualifies as protected “personal-related data” or “sensitive infrastructure data”.
The UK Information Commissioner’s Office (ICO) recently clarified in updated guidance: data encryption is not merely a technical requirement but a legal confirmation of data control authority. This means owning encryption keys and managing key security is no longer optional—it is a legal obligation.
Risks Are No Longer Theoretical—They’re Real
Norway’s Ruter Case Study: Remote Control Reality
In 2024, Norwegian public transport company Ruter conducted a revealing test. They brought a Chinese-manufactured electric bus and a Dutch-manufactured electric bus into an underground mine for cybersecurity testing. The results were alarming: The Chinese-manufactured bus possessed remote access capability—the manufacturer could access and control battery systems, power management systems, and other critical components through data connections. The Dutch-manufactured bus lacked such remote access capability.
Ruter’s conclusion was starkly direct: theoretically, the Chinese bus could be remotely stopped or rendered inoperable by the manufacturer. What is the lesson from this case? It demonstrates that remote access and remote control are not theoretical risks but real, verifiable, and consequential capabilities.
Identical Risks Exist in Energy Storage Systems
Energy storage systems are more complex and more critical than buses. When we discuss an energy storage system being “remotely stopped,” we are discussing not merely equipment failure but threats to grid power stability.
Currently, many commercial energy storage systems do possess remote management capabilities—for software updates, performance diagnostics, remote monitoring. But the critical question is: who provides these remote access capabilities, who controls them, and how is misuse prevented?
Local Control vs. Cloud-Based Systems: Beyond Technical Considerations
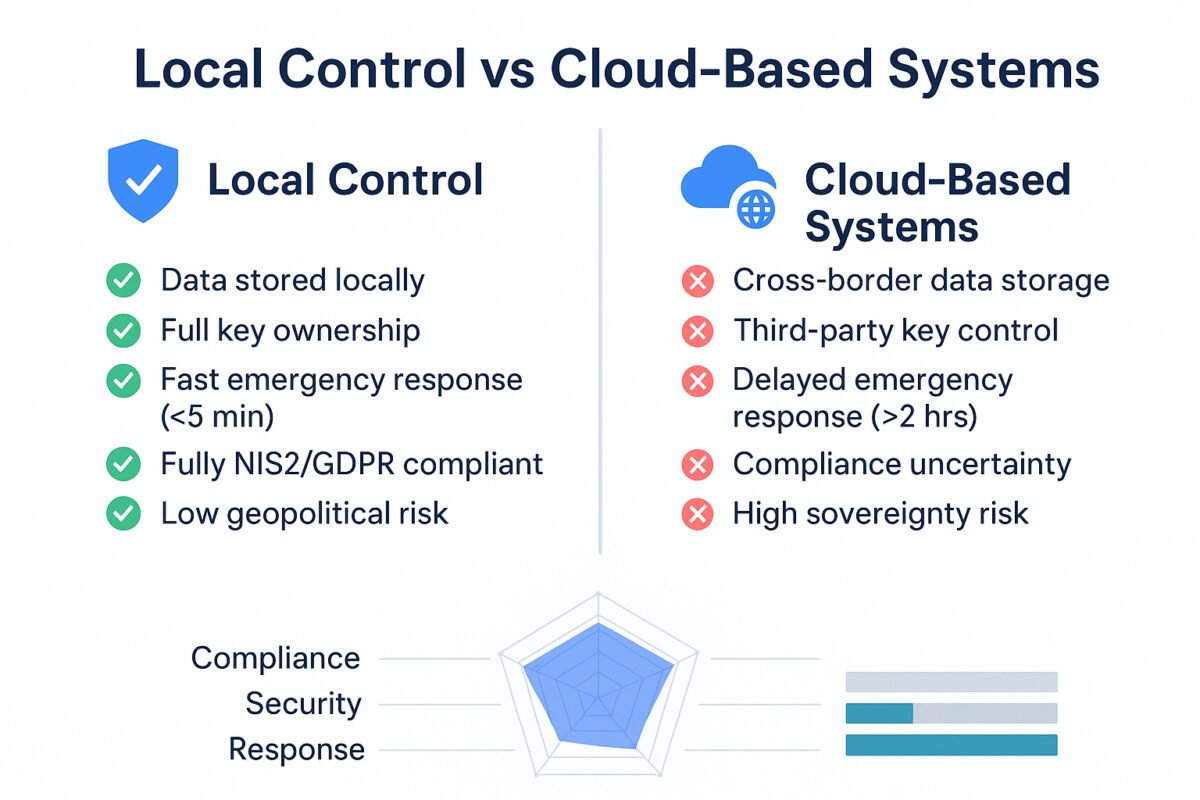
Many might ask: why not trust cloud service providers to manage our data? The answer is not simple.
Hidden Risks of Cloud-Based Systems
- Legal Risks from Geographic Location: Data might be stored anywhere. Legal frameworks vary dramatically across regions. An operation legal in the EU may be illegal in China, or vice versa. Your data could suddenly be transferred to a new jurisdiction without your ability to prevent it.
- Third-Party Dependency: By relying on a cloud service provider, you assume the risk that this provider might be acquired, collapse, or face political interference. 2024’s geopolitical landscape demonstrates these risks are no longer theoretical.
- Remote Access Transparency Issues: “Remote access” in cloud systems often operates as a black box. You don’t know who accessed what data when. Audit logs might be tampered with, and you cannot truly verify activity.
- Emergency Response Delays: When security incidents occur, you need immediate response. But if you depend on a cloud service provider, your response speed becomes constrained by a third party. In energy systems, such delays carry real consequences.
Strategic Advantages of Local Control
What does local control provide conversely?
- Complete Data Sovereignty: Your data physically resides in places you can manage, and you possess complete legal rights to data access. This not only satisfies GDPR but, more importantly, ensures complete control over your business.
- Transparent Audit Chain: All data access and all system operations can be completely recorded and audited. You can independently prove system compliance to regulators without relying on third-party claims.
- Independent Security Decision-Making: You need not await cloud provider security patches. When vulnerabilities are discovered, you can immediately act. In critical infrastructure,this speed difference can be life-and-death critical.
- Regulatory Compliance Certainty: When NIS2 and ESA frameworks formally take effect, locally-controlled systems will directly satisfy requirements, while cloud-based systems may require redesign or face non-compliance risks.
Data Encryption and Key Management: Where Real Differences Lie
Many suppliers claim “our systems are encrypted.” But this statement omits a critical question: who owns the encryption keys?
Why Key Ownership Matters
Encryption is a technical detail, but who controls encryption keys represents a strategic question. Imagine a scenario: your storage system adopts a cloud-based approach with all encryption keys managed by the cloud provider. Now consider what occurs:- Government regulators request your system operational data for compliance review. You cannot provide it directly—you must request the cloud provider decrypt and deliver it. How much delay occurs? What leakage risks emerge?- You need to quickly stop or start a storage unit to address grid emergencies. You must operate through the cloud provider’s API. What if their service is temporarily unavailable?- You need to prove that no unauthorized access altered data in your system. Whose audit logs do you rely upon? How can you confirm these logs have not been tampered with?
Value of Local Key Management
Conversely, if you control encryption key authority:- Legal Autonomy: You can directly, independently prove your system’s compliance to regulators- Operational Autonomy: You can immediately respond to any situation- Security Autonomy: You can verify your system’s security without depending on any third-party claims. This represents the core value of local control solutions.
Solutions Emerging in UK and European Markets: New Paradigm of Local Partnership
Against this backdrop, a new solution paradigm is forming in UK and European energy markets: deep partnership between local BMS suppliers and local energy management platforms.
Complete Local Ecosystem
When a local BMS provider (for instance, solutions from energy storage innovation ecosystems like Lithium Valley) engages in deep partnership with a local energy management operations platform (such as Brill Power), what occurs? The entire data flow, control flow, and decision flow remains within a local, controllable, auditable ecosystem. This means:- Complete chain from collection to decision remains local: Battery data collected from management units, encrypted, stored, analyzed, and presented to operators—the entire process completes on UK or EU infrastructure- Complete operator visibility: Platform users possess complete understanding and control capabilities over every system state, every data access, and every control command- Rapid local response: When any anomaly or emergency occurs, response is completed immediately by local teams rather than awaiting any overseas party
Unified Security Standards
When such local partnership establishes itself, the parties jointly establish a unified, high-standard security and data protection standards framework:- Key Management: All encryption keys are controlled by the operations party, fully compliant with UK GDPR requirements- Access Controls: Strict multi-factor authentication, permission management, comprehensive audit logs- End-to-End Encryption: All communications from BMS to EMS employ international-grade encryption standards (AES-256 or higher)- Continuous Monitoring: Real-time anomaly detection, intrusion protection, threat response. These are not marketing promises but verifiable, auditable, legally-binding technological and procedural commitments.
Practical Value for Operators
For large operators like Stagecoach, FirstBus, or any energy company and infrastructure enterprise operating storage systems, what is the value of local control solutions?
Compliance Advantages
When NIS2 directive requirements are enforced, you already satisfy them- When UK ESA framework takes effect in 2026, your system already fully complies- You avoid expensive future system retrofits or non-compliance risks
Operational Advantages
Systems remain fully under your control, independent of any overseas connectivity- In any network disruption scenario, your system continues normal operation- In any emergency, you can immediately make decisions and take action
Commercial Advantages
While initial investment may slightly exceed cloud solutions, long-term you avoid continuous cloud service costs- More importantly, you avoid future regulatory risks and potential fines- You can announce to investors, government, and public: my system is completely locally controlled and data is fully protected
Strategic Advantages
Your energy future remains insulated from geopolitical factors- You participate in building UK and European energy security infrastructure, not depending on overseas supply chains- In an era of global turbulence, such local autonomy has become an increasingly important competitive factor
Significance for Government and Decision-Makers
From a national strategy perspective, why do locally-controlled energy storage systems matter?
National Security
Energy infrastructure represents the core of national security. When critical control points of your energy systems rest in overseas hands, you have in some measure surrendered energy security to others. Local control means in any circumstance, your energy destiny remains in your own hands.
Regulatory Certainty
GDPR, NIS2, ESA—these represent clear legal frameworks. Locally-controlled systems can clearly demonstrate compliance without complex legal interpretation.
Emergency Response Capability
During any energy crisis or cybersecurity incident, government must directly interact with systems. Local control means government can directly understand situations and directly intervene without requiring any third party.
Industrial Strategy
Supporting local, secure, compliant energy storage solutions aligns with UK government strategy regarding energy transition, green growth, and economic security.
Technology and Commerce Converge: Why Now Is Critical
Why is this moment so critical for local energy storage solutions?
Regulatory Pressure: NIS2 is already effective; ESA framework is coming. This is not future possibility but present reality.Geopolitical Reality: 2024’s events clearly demonstrate that energy autonomy has become central to national strategy. In this context, systems dependent on overseas suppliers face political and legal pressure.Technical Maturity: Local BMS technology is highly mature. Local energy management platforms can now handle complex operational requirements. What historically might have been lacking is market demand as driving force. Now, this driving force has arrived.Commercial Opportunity: For operators and investors making strategic choices now, they will gain significant competitive advantages. Similarly, for enterprises providing localized solutions, this period represents a critical opportunity in industry transformation.
Conclusion: The Moment of Choice
The future of energy storage is being redefined. This redefinition’s core questions are: whose data is it, who holds control authority, and who can rapidly respond when problems arise? Historically, the answer to these questions was always: “leave it to cloud service providers; they’re more professional.” But now this answer no longer holds. Legal frameworks, geopolitical reality, and technological progress advancement all point in a new direction: local control, data sovereignty, autonomous security. Now, UK and European markets are witnessing the emergence of deep partnerships between local BMS suppliers and local energy management platforms, offering energy operators a genuinely viable, compliant, strategic alternative. For any decision-maker responsible for energy infrastructure, the question is no longer “should we use cloud-based systems” but rather “when should we migrate to local control solutions”. The answer is simple: the sooner the better.
Key Comparison Table
Dimension | Local Control | Cloud-Based Systems |
Data Sovereignty | Fully locally managed | Cross-border, sovereignty risk |
Regulatory Compliance | Immediately satisfies NIS2, GDPR, ESA | Requires assessment and retrofit |
Key Management Authority | Operations fully control | Third-party dependent |
Audit Transparency | Complete, real-time, verifiable | Supplier-dependent reporting |
Emergency Response | <5 minutes | >2 hours |
5-Year TCO | Moderate + Low risk | Low + High risk costs |
Geopolitical Risk | Low | High |
System Independence | Fully independent | Supplier-dependent |
































.png)
.png)
.png)
.png)